1. Explain the triple constraint and its importance in project management.
The triple constraint involves making trade offs between scope, time and cost for a project. It is inevitable in a project life cycle that there will be changes to the scope, time or cost of the project. The three variables are interdependent: you cannot change one without changing the others. There is a high failure rate in IT projects between 30 and 70 per cent due to late delivery, exceeding budget, or not delivering what was agreed upon. A successful project is typically on time, within budget, meets the business' requirements and fulfills the customer's needs.
The triple constraint involves making trade offs between scope, time and cost for a project. It is inevitable in a project life cycle that there will be changes to the scope, time or cost of the project. The three variables are interdependent: you cannot change one without changing the others. There is a high failure rate in IT projects between 30 and 70 per cent due to late delivery, exceeding budget, or not delivering what was agreed upon. A successful project is typically on time, within budget, meets the business' requirements and fulfills the customer's needs.
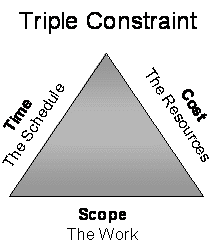
2. Describe the two primary diagrams most frequently used in project planning.
The two primary diagrams used in project planning include PERT (program evaluation and review technique) and Gantt charts. PERT charts are a graphical network model that depicts a project's tasks and the relationships between those tasks. Gantt charts are a simple bar chart that depicts project tasks against a calendar.
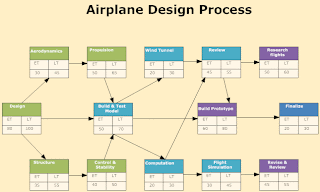
An example of a PERT chart
A project manager must focus on managing three primary areas to ensure success: managing people, managing communications and managing change. Managing people is one of the hardest and most critical efforts a project manager untertakes. Resolving conflict within the team and balancing the needs of the project with the personal and professional needs of the team are two of the challenges facing project managers.
4. Outline two reasons why projects fail and two reasons why projects succeed.
Two reasons why projects fail include: failure to align project with organizational objectives, and inability to move beyond individual and personality conflicts.
Two reasons why projects succeed include: good communication and team members are working towards a common goal.











